In order to successfully deploy and manage containerized applications, understanding the essentials of Kubernetes installation is crucial.
Before you begin
Ensure that your **Linux distribution** is up-to-date before attempting to install **Kubernetes**. Check if the **systemd** service is running properly, as it is crucial for managing services in Linux. Familiarize yourself with the basics of **cloud computing** to understand how Kubernetes operates in a virtual environment.
Make sure your system meets the minimum requirements for running Kubernetes, such as sufficient **memory** and **CPU** resources. Configure your **network interfaces** correctly to ensure communication between nodes in a **computer cluster**. Install necessary packages using your distribution’s **package manager** to prepare for Kubernetes installation.
Understand the **booting** process of your Linux system to troubleshoot any issues that may arise during Kubernetes installation. Follow best practices for configuring **network settings** and **firewalls** to secure your Kubernetes environment. Regularly update your system to patch any **software bugs** that could potentially impact Kubernetes functionality.
Check network adapters
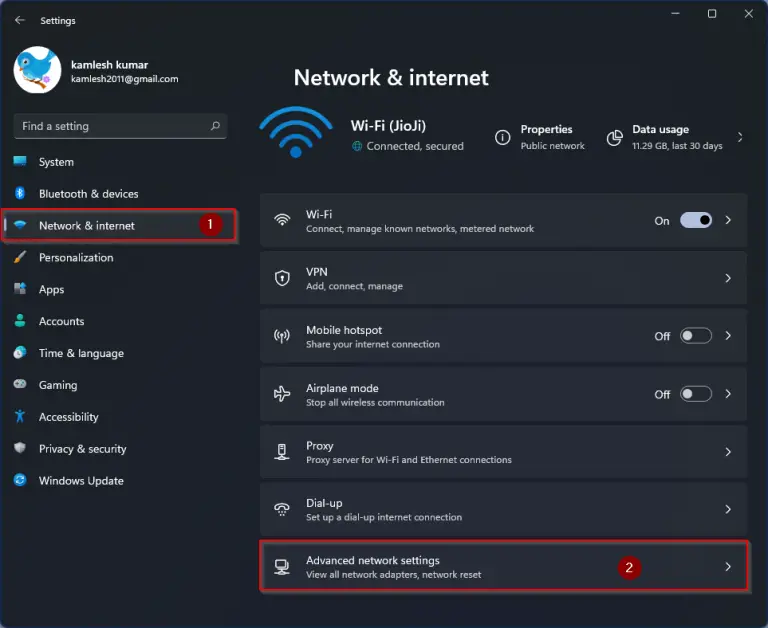
To ensure a smooth Kubernetes installation, it is crucial to check your network adapters. Network adapters play a vital role in communication between nodes within a cluster, so it is important to verify that they are properly configured and functioning correctly.
Before proceeding with the installation process, use commands such as ifconfig to inspect the status of your network interfaces. Make sure that the correct IP addresses, subnet masks, and gateway addresses are set up to enable seamless communication between nodes.
Additionally, check for any network adapter errors or issues that may hinder the installation process. Troubleshoot any connectivity problems and ensure that your network adapters are able to communicate with other nodes effectively.
By verifying and ensuring the proper functionality of your network adapters, you can avoid potential connectivity issues and ensure a successful Kubernetes installation. This step is essential in creating a stable and reliable cluster environment for your applications to run smoothly.
Check required ports
Verify networking: In addition to checking ports, it’s important to verify that your network configuration is properly set up for Kubernetes. This includes ensuring that all nodes in the cluster can communicate with each other over the network. Utilize tools like ifconfig or netcat to check network interfaces and connectivity between nodes.
Secure access: To maintain security, consider setting up firewalls or network policies to restrict access to certain ports and services within your Kubernetes cluster. Utilize tools like sudo for administrative access control and configure secure authentication mechanisms to prevent unauthorized access to your cluster.
Installing a container runtime
To install a container runtime for Kubernetes, you can choose from options such as Docker, Containerd, or CRI-O. For Docker, ensure you have the correct version that is compatible with Kubernetes. Use your Linux distribution’s package manager to install the runtime. If you encounter any issues, refer to the official documentation for troubleshooting steps.
Once the container runtime is installed, configure it to work with Kubernetes. This typically involves adjusting configuration files and ensuring the runtime is set up to communicate with the Kubernetes API server. Make sure the runtime is running as a systemd service to ensure it starts automatically on boot.
Test the container runtime by deploying a simple container using a Kubernetes pod. This will help verify that the installation was successful and that the runtime is functioning correctly.
Installing kubeadm, kubelet, and kubectl
To install **kubeadm**, **kubelet**, and **kubectl**, you can follow these steps:
1. Start by updating your package index and installing necessary tools like curl and apt-transport-https.
2. Add the Kubernetes signing key and repository to your system.
3. Install the required packages using apt-get or yum, depending on your Linux distribution.
4. Make sure all necessary packages are installed and up to date.
5. Verify the installation by checking the versions of kubeadm, kubelet, and kubectl.
Once you have successfully installed these essential components, you will be ready to start setting up and managing your Kubernetes cluster.
Configuring a cgroup driver
To configure a cgroup driver for Kubernetes installation, you need to first determine which cgroup driver your system is currently using. Common cgroup drivers include cgroupfs and systemd.
If your system is using cgroupfs, you’ll need to ensure that the cgroup driver is specified in the kubelet configuration file. This can be done by adding the “–cgroup-driver=” flag followed by “cgroupfs” to the kubelet service file.
On the other hand, if your system is using systemd as the cgroup driver, you’ll need to specify this in the kubelet configuration file with the “–cgroup-driver=” flag followed by “systemd”.
After making these changes, restart the kubelet service for the changes to take effect. It’s important to verify that the cgroup driver has been successfully configured before proceeding with the Kubernetes installation.
Learning environment
Having a good grasp of operating systems like Red Hat Enterprise Linux, Ubuntu, CentOS, Fedora, and Debian will also be beneficial in navigating the installation process. Additionally, knowledge of networking fundamentals and protocols, such as Internet Protocol and MAC addresses, will be essential for setting up a functional Kubernetes environment.
Understanding basic computer hardware components, like CPUs and memory, will also aid in optimizing your Kubernetes installation. Consider exploring tools like Docker for containerization and netcat for network debugging to enhance your learning experience.
Production environment
Red Hat Enterprise Linux and Ubuntu are popular choices for hosting Kubernetes clusters, but make sure your chosen OS is compatible with Kubernetes.
Consider factors like network interfaces, memory management, and CPU allocation to ensure optimal performance of your Kubernetes setup.
Follow best practices for configuring your environment, including setting up private networks, managing storage with Fstab, and securing your system with tools like Sudo.
Software prerequisites
Additionally, make sure your system has the necessary memory (RAM) and CPU resources to support the installation and operation of Kubernetes. A reliable network connection is also crucial for communication between nodes in the cluster.
It’s important to have a basic understanding of **networking**, **cloud computing**, and **operating systems** to effectively set up and manage Kubernetes. Taking Linux training can be beneficial in gaining the necessary skills for working with Kubernetes.
Lastly, familiarize yourself with **Docker** as Kubernetes often works in conjunction with containerized applications. By having these software prerequisites in order, you’ll be better prepared for a successful Kubernetes installation.
Hardware prerequisites
When setting up Kubernetes, ensure your hardware meets the necessary prerequisites.
You will need a minimum of 2 GB of RAM to run Kubernetes efficiently.
Additionally, make sure your CPU has at least 2 cores to handle the workload.
It is also important to have a stable internet connection, as Kubernetes relies on communication between nodes.
Consider using a private network to ensure security and avoid potential external threats.
Ensure your hardware supports virtualization, as Kubernetes often runs on virtual machines.
By meeting these hardware prerequisites, you can ensure a smooth installation and operation of Kubernetes on your system.
Install OvalEdge
Once downloaded, use the kubectl command to apply the OvalEdge YAML files to your Kubernetes cluster.
Make sure to specify any necessary configurations, such as memory limits or persistent storage, in the YAML files before applying them.
After applying the files, use kubectl to check the status of the OvalEdge pods to ensure they are running successfully.
Finally, access the OvalEdge dashboard using the specified URL to start using the platform for data management and analytics.
Create a cluster
Next, install Docker, which is essential for running containers in Kubernetes. Once Docker is set up, you can proceed with installing Kubernetes using a tool like kubeadm. Follow the official Kubernetes documentation for detailed instructions on the installation process.
After Kubernetes is installed, you can start setting up your cluster by creating a master node and joining worker nodes to it. Make sure to configure networking, storage, and security settings according to best practices.
Regularly update your Kubernetes installation to ensure it is secure and up-to-date with the latest features and bug fixes. Consider taking Linux training to deepen your understanding of Kubernetes and improve your cluster management skills.
Summary
Kubernetes Installation Essentials
When setting up Kubernetes, ensure to have a strong understanding of Linux systems to navigate the installation process smoothly. Start by choosing a compatible Linux distribution like Fedora, CentOS, Debian, or Alpine Linux. Familiarize yourself with essential concepts such as memory management, networking, and CPU allocation.
Ensure that your system meets the necessary hardware requirements, including sufficient RAM and CPU resources. Pay attention to details like MAC addresses and network interfaces to configure your nodes correctly. Understanding concepts like memory paging and booting processes will be crucial for a successful installation.
Utilize tools like Docker for containerization and API integration.
Components
The kube-apiserver acts as the front-end for Kubernetes, handling all communication and serving the API. The kube-controller-manager manages different controllers that regulate the state of the cluster. The kube-scheduler is responsible for placing workloads onto nodes based on resource requirements.
Etcd is a distributed key-value store used to store all cluster data. The kubelet is an agent running on each node, responsible for managing the containers. Lastly, kube-proxy is a network proxy that maintains network rules.
Understanding these components is crucial for a successful Kubernetes installation and operation. Be sure to familiarize yourself with each one to effectively manage and scale your Kubernetes cluster.
Pre-requisites
Before diving into Kubernetes installation, ensure you have a solid understanding of Linux operating systems. Familiarize yourself with basic concepts such as memory paging and network interfaces.
Having knowledge of operating system fundamentals, like Fedora Linux or Alpine Linux, will be beneficial. Understanding concepts like MAC addresses and private networks will also be helpful during the installation process.
Make sure you have the necessary hardware requirements, including a sufficient amount of RAM and CPU. It’s also important to have a stable internet connection for downloading necessary software and updates.
Consider taking a Linux training course to enhance your skills and prepare yourself for working with Kubernetes and other related technologies. This will set you up for success and ensure a smooth installation process.
Troubleshooting
– When facing issues during Kubernetes installation, start by checking the system requirements and ensuring all prerequisites are met.
– Verify that your system has enough resources such as RAM and CPU for smooth operation.
– Check the network configuration, including IP addresses and MAC addresses, to ensure proper communication between nodes.
– Ensure that all necessary software components, such as the operating system and necessary libraries, are properly installed and up to date.
– Troubleshoot any errors related to port conflicts or connectivity issues within the computer cluster.
– Use diagnostic tools and logs to identify and resolve any software bugs or compatibility issues that may arise.
– Following these steps will help streamline the Kubernetes installation process and ensure a successful deployment.















