Welcome to our comprehensive tutorial on web application development. In this article, we will guide you through the essential steps and best practices to create dynamic and functional web applications. Let’s dive in and unlock the world of web development together.
Getting Started with Web Development
To **get started** with **web development**, you first need to have a solid understanding of **HTML** and **CSS**. These are the building blocks of any website or web application. Once you are comfortable with these, you can move on to learning **JavaScript** to add interactivity to your web pages.
Next, consider learning a **CSS framework** like **Bootstrap** or **Sass** to make styling your websites easier and more efficient. These frameworks provide pre-built components and styling that you can use in your projects.
If you are interested in **web design**, you may want to explore tools like **Photoshop** or **Sketch** to create mockups and designs before implementing them in code. Understanding **user behavior** and **user experience** is also important in creating successful web applications.
For **server-side** development, you may want to learn a **backend** language like **PHP**, **Python** with **Django**, or **JavaScript** with **Node.js**. These languages allow you to build the logic and functionality of your web applications.
Consider using **version control** software like **Git** to track changes in your code and collaborate with others. This is essential for working on larger projects and ensuring that your code is safe and secure.
Essential Skills for Web Developers
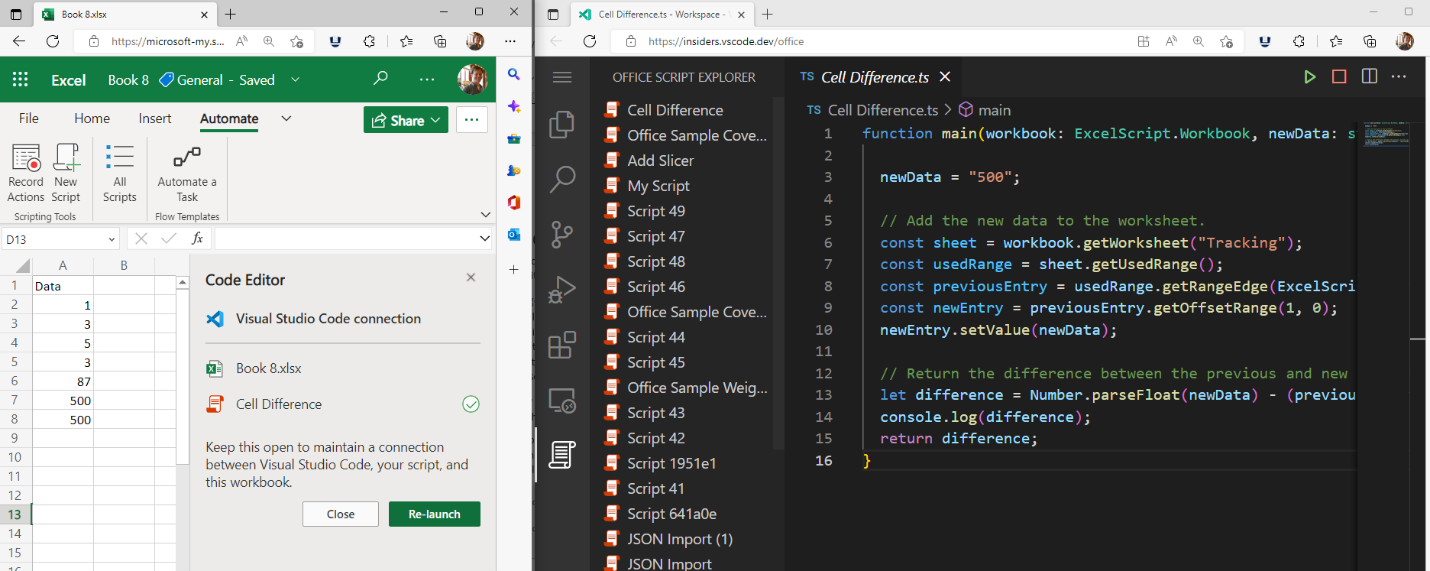
To excel in web application development, **web developers** need to possess a strong foundation in **HTML** and **CSS**. These are the building blocks of any website, determining the structure and design elements. **JavaScript** is another essential skill, enabling developers to create interactive and dynamic web pages.
Understanding **server-side** programming languages like **PHP** or **Python** is crucial for handling data and user interactions on the server. Familiarity with **databases** and **SQL** is also necessary to store and retrieve information efficiently.
Version control systems like **Git** allow developers to manage code changes effectively. Knowledge of **responsive web design** ensures that websites are accessible on various devices.
**Web frameworks** like **React**, **Django**, or **Flask** provide tools and libraries to streamline development processes. Continuous learning and staying updated with the latest technologies are vital for web developers to keep pace with the ever-evolving web landscape.
Popular Frontend Technologies and Frameworks
When it comes to **frontend technologies and frameworks** for web application development, there are a few popular options that developers often turn to. One of the most widely used frameworks is **React**, which is known for its flexibility and performance. Another important aspect of frontend development is **page layout**, which can be achieved using CSS frameworks such as **Sass** to ensure a responsive design.
Frameworks like **Django** and **Flask** help streamline backend development, while also offering scalability and security features. These frameworks are built on **Python**, a versatile and powerful programming language. Leveraging these tools can help developers create dynamic and interactive web pages that cater to modern user behavior and technology.
It’s important to stay up-to-date with the latest trends in web development, such as **Web 2.0** and **semantic web** technologies.
Introduction to Backend Development
Backend development is a crucial aspect of web application development, focusing on the server-side operations that power websites and applications. This involves working with databases, servers, and APIs to ensure seamless functionality and performance. Understanding backend development is essential for creating dynamic and interactive web experiences.
Linux training is highly recommended for those interested in backend development, as many servers run on Linux systems. This training will provide you with the necessary skills to work effectively in a Linux environment. By mastering backend development, you can build scalable and efficient web applications that meet the demands of modern users.
With tools like Django and Flask, developers can easily create powerful backend systems using Python, a versatile and widely-used programming language. These frameworks provide the structure and functionality needed to build robust web applications. Embracing backend development is a key step towards becoming a proficient web developer.
Exploring Backend Technologies
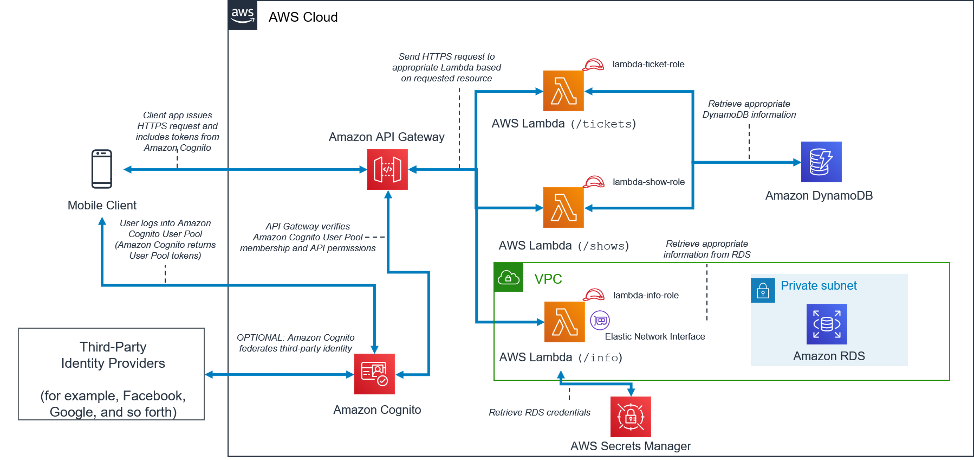
When exploring **backend technologies** for **web application development**, it is essential to understand the importance of choosing the right tools and frameworks. **Python** and **Django** are popular choices for backend development due to their scalability and ease of use.
**Flask** is another great option for building web applications, offering a lightweight framework that is ideal for smaller projects. Understanding **SQL** and database management is crucial for backend development, as it allows you to store and retrieve data efficiently.
**Open-source software** is a valuable resource for developers, providing access to a wide range of tools and libraries. By familiarizing yourself with these technologies, you can create powerful and responsive web applications that meet the needs of users across different platforms.
Setting Up Your Developer Environment
To set up your developer environment for web application development, you will need to start by choosing the right **operating system**. Many developers prefer using **Linux** for its flexibility and compatibility with a wide range of tools and technologies.
Next, you should install a text editor or an integrated development environment (IDE) that supports **web development** languages such as **HTML, CSS, and JavaScript**. Popular choices include **Visual Studio Code** and **Sublime Text**.
You will also need to install **Node.js** and **npm** to manage dependencies and run scripts for your web application. These tools are essential for building **React** applications and other **JavaScript** frameworks.
Consider using **Google Chrome** or **Firefox** as your primary **web browser** for testing and debugging your web applications. These browsers have robust developer tools that can help you identify and fix issues.
Finally, make sure to set up a **version control system** such as **Git** to track changes in your codebase and collaborate with other developers effectively. This will ensure that your web application development process is **efficient** and **organized**.
Creating Your First Webpage
To create your first webpage, start by writing the basic structure in a markup language like HTML. Use tags for important headings and paragraphs to make your content stand out.
Next, add a style sheet to enhance the page layout and design. This will help your webpage look professional and visually appealing.
Test your webpage in different browsers like Firefox and Google Chrome to ensure compatibility across platforms.
Consider using a responsive web design to make your webpage accessible on various devices like tablets and phablets.
You can also explore frameworks like React or Django to simplify the development process.
Remember to keep your code clean and organized for easier maintenance and updates.
Lastly, don’t be afraid to experiment and learn from resources like W3Schools or online tutorials to enhance your web development skills.
The Next Steps in Web Development
In the world of web development, the next steps involve diving into advanced frameworks like Django and Flask. These tools provide a solid foundation for building powerful web applications that can handle complex tasks and data processing.
By learning these frameworks, you can take your web development skills to the next level and create dynamic, interactive web applications that deliver a seamless user experience. Dive into Python programming to fully utilize the capabilities of these frameworks, and unlock the potential of your web development projects.
With the rise of cross-platform software and the increasing demand for responsive web design, mastering these advanced tools is essential for staying competitive in the field of web development. Take the time to explore these frameworks and experiment with different libraries and tools to find the best fit for your projects.
Continue your journey in web development by delving deeper into the world of open-source software and discovering new ways to enhance your web applications. Stay updated on the latest trends and advancements in web development to ensure that your skills remain relevant in this ever-changing industry.
Useful Resources and Links
| Resource |
Description |
Link |
| MDN Web Docs |
Comprehensive web development documentation |
Visit |
| W3Schools |
Online web development tutorials |
Visit |
| Stack Overflow |
Community-driven question and answer site for programming |
Visit |
| GitHub |
Version control platform for collaboration on code |
Visit |