Discover the top Kubernetes testing tools that will streamline your deployment process and ensure reliable performance for your applications.
Scale Testing Workflow with Kubernetes
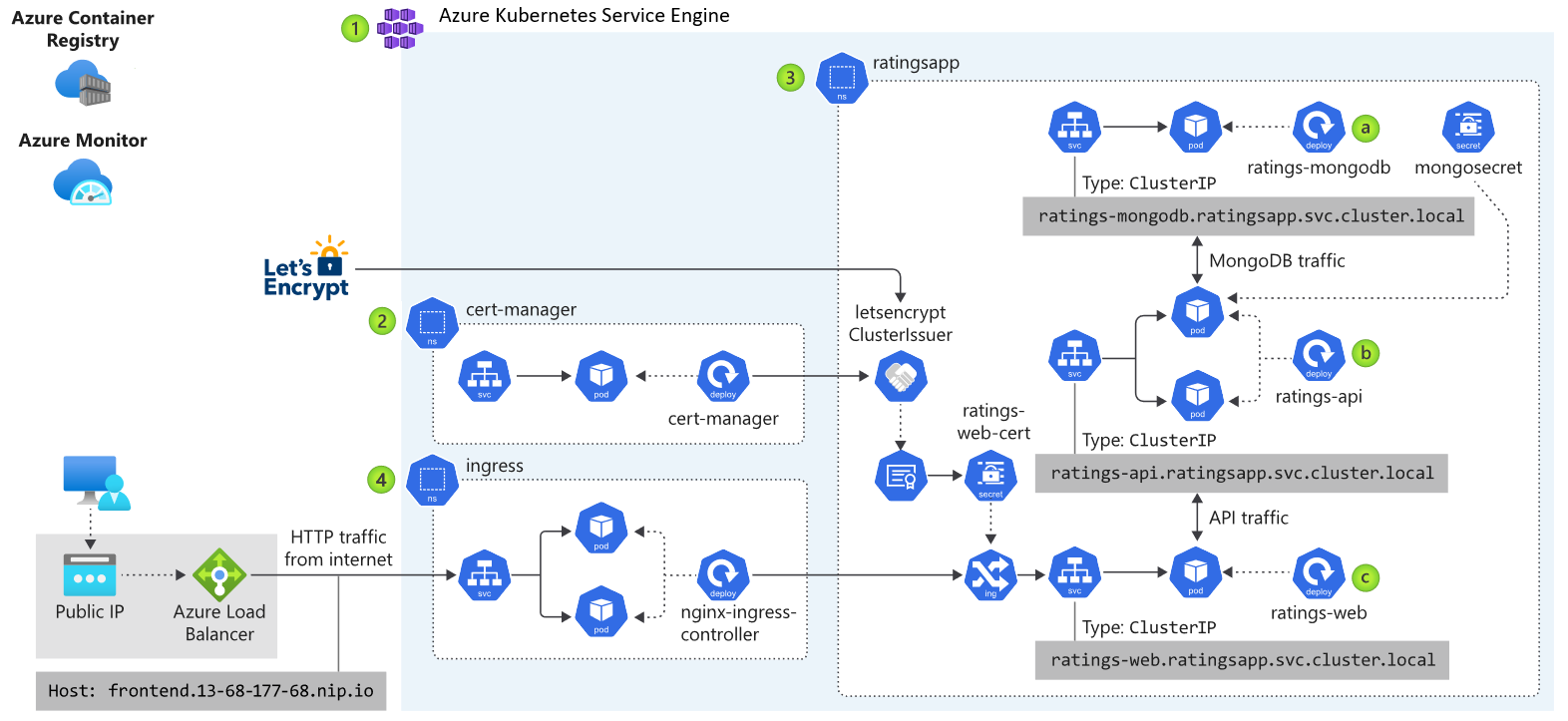
By incorporating these tools into your testing process, you can gain valuable insights into your application’s scalability and performance under various conditions. This proactive approach to testing can help you identify and address potential issues before they impact your users, ultimately improving the reliability and stability of your applications.
In addition to scale testing, Kubernetes also supports other testing practices such as continuous integration and test automation. By leveraging Kubernetes’ capabilities for deploying and managing containerized applications, you can streamline your testing workflows and ensure consistent and reliable results across different environments. These tools and practices are essential for modern DevOps teams looking to deliver high-quality software at scale.
Simplified Test Execution
For continuous integration, consider using **GitHub** for version control and **Docker** for scalability. **Python** and **JavaScript** are useful for scripting and frontend/backend testing.
Don’t forget about security – tools like **Transport Layer Security** and **HTTP/2** can help protect your applications. And for monitoring, **Dashboard** tools can provide valuable insights into your deployment environment.
Centralized Quality Control
One such tool is **GitHub**, which allows for seamless collaboration and version control among team members. **Ansible** is another valuable tool that can automate your testing processes, saving time and reducing the risk of human error. By incorporating these tools into your testing environment, you can ensure that your Kubernetes applications are thoroughly tested and optimized for performance.
In addition to these tools, consider implementing **unit testing** to validate individual components of your application, and **chaos engineering** to test its resilience under unpredictable conditions. This comprehensive approach to testing will help you uncover potential vulnerabilities and ensure the reliability of your Kubernetes deployment environment.
Kubernetes-Powered Test Platform
With features like **namespace isolation** and **container orchestration**, Kubernetes provides a robust framework for running tests in parallel across multiple clusters. This allows you to simulate real-world scenarios and identify potential issues before deployment.
By incorporating tools like **GRPC** for communication and **Chaos engineering** for resilience testing, you can create a comprehensive testing strategy that covers all aspects of your application’s functionality. Kubernetes testing tools offer a seamless integration with other DevOps tools, making it easy to incorporate testing into your CI/CD pipeline.
Testing Tools Integration
**GRPC** is another testing tool that can be integrated with Kubernetes to test communication between microservices using high-performance RPC framework. Additionally, tools like **Docker** and **HTTP** can be utilized to test containerized applications and API endpoints within a Kubernetes environment.
By integrating these testing tools with Kubernetes, developers can ensure the reliability and performance of their applications in a cloud-native environment. These tools provide a seamless way to automate testing processes, identify bugs, and improve overall application quality in a Kubernetes cluster setup.
Kubernetes Testing Automation
For those looking to automate their testing processes, **LitmusChaos** provides a framework for chaos engineering in Kubernetes, allowing you to inject faults and test the resilience of your applications. **Kube-bench** is another valuable tool for security testing, providing CIS benchmarks for Kubernetes clusters.
By incorporating these **Kubernetes testing tools** into your workflow, you can ensure the reliability and security of your applications running on Kubernetes clusters.
Focus on Test Development
When focusing on ***test development*** in Kubernetes, it’s essential to choose the right tools to ensure the effectiveness and efficiency of your testing process. Two popular tools for this purpose are ***Ginkgo*** and ***Gomega***, which work seamlessly together to provide a powerful testing framework for Kubernetes applications.
***Ginkgo*** is a BDD-style testing framework that allows developers to write clear and concise tests using the popular Go programming language. It provides a structured way to define test cases and suites, making it easy to organize and run tests for Kubernetes applications.
***Gomega*** is a matcher framework that complements ***Ginkgo*** by providing a rich set of matchers for asserting the behavior of Kubernetes applications. With ***Gomega***, developers can write expressive and readable test assertions, making it easier to understand the expected outcomes of tests.
By leveraging these two tools in your test development process, you can ensure that your Kubernetes applications are thoroughly tested and validated, leading to more reliable and resilient software deployments.
Testing Safety Measures

One popular tool for testing safety measures in Kubernetes is Ansible, which allows for automation of testing processes across multiple nodes. Another useful tool is Puppet, which helps in managing configurations and ensuring consistency in testing environments. These tools can be integrated seamlessly into your Kubernetes testing workflow.
In addition to these tools, it is important to regularly test for vulnerabilities and bugs in your Kubernetes clusters. Tools such as Go programming language and Python can help in writing scripts for vulnerability testing and debugging. Regular testing ensures that your Kubernetes clusters are secure and reliable for deployment.
By utilizing these testing tools and best practices, you can ensure that your Kubernetes clusters are safe and secure for running your applications. Regular testing and automation play a crucial role in maintaining the reliability and security of your Kubernetes infrastructure.
Community Support for Testing Tools
Community support for **testing tools** is crucial for ensuring the success of your **Kubernetes** projects. When choosing a testing tool, consider the level of community engagement and support available. Look for tools with active forums, documentation, and regular updates.
Having a strong community behind a testing tool means you’ll have access to a wealth of knowledge and resources to help troubleshoot issues and optimize your testing processes. Community support can also provide valuable insights and best practices for using testing tools effectively within a **Kubernetes** environment.
Whether you’re new to **Kubernetes** testing or looking to enhance your current testing strategy, leveraging community support for testing tools can make a significant difference in the success of your projects. Be sure to engage with the community, ask questions, and contribute back to help strengthen the ecosystem of **Kubernetes** testing tools.
Stay Updated with Kubernetes Testing Trends
Stay Updated with Kubernetes Testing Trends by exploring the top Kubernetes Testing Tools. These tools are essential for ensuring the reliability and efficiency of your Kubernetes applications.
With the rapid growth of Kubernetes in the industry, it’s crucial to stay informed about the latest testing trends and tools. By leveraging these tools, you can streamline your testing process and improve the overall quality of your applications.
From test automation to unit testing, these tools cover a wide range of testing capabilities that are essential for Kubernetes development. Keep an eye out for new tools and updates from the Cloud Native Computing Foundation to stay ahead of the curve.
By incorporating these Kubernetes testing tools into your workflow, you can optimize your testing process and ensure the seamless operation of your applications in a Kubernetes environment. Don’t miss out on the latest advancements in Kubernetes testing – stay informed and stay ahead.