In the world of modern software development, ensuring the security of microservices is paramount. This article serves as the ultimate guide to implementing best practices for securing your microservices architecture.
Understanding Microservices Security

When it comes to **microservices security**, it’s crucial to prioritize **secure communication** between services. Implementing **Transport Layer Security (TLS)** can help ensure data is encrypted and protected from potential threats. Additionally, **access control** mechanisms should be in place to limit who can interact with each service.
Regularly conducting **security audits** and **vulnerability assessments** can help identify and address any weaknesses in your microservices architecture. **Authentication** and **authorization** protocols should be robust to prevent unauthorized access to sensitive data.
It’s also important to consider **secure coding practices** when developing microservices. By following **best practices** and incorporating **security principles** into the **software development life cycle**, you can build more **secure and reliable** services.
Ultimately, a comprehensive **microservices security strategy** should address not only technical aspects, but also factors such as **risk management** and **operational efficiency**. By prioritizing security from the start and continuously evaluating and improving your practices, you can better protect your microservices architecture from potential **data breaches** and other security threats.
Utilizing Authentication and Authorization Methods
When it comes to securing your microservices, utilizing **authentication** and **authorization** methods is crucial. Authentication ensures that users are who they claim to be, while authorization controls what actions they can perform within the system.
Implementing strong authentication methods such as **OAuth** or **JWT** can help prevent unauthorized access to your microservices. Additionally, using role-based access control (RBAC) can ensure that users only have access to the resources they need.
Regularly reviewing and updating your authentication and authorization mechanisms is essential to stay ahead of potential threats. This includes monitoring for any **vulnerabilities** or weaknesses in your system that could be exploited by malicious actors.
Creating API Gateways for Microservices
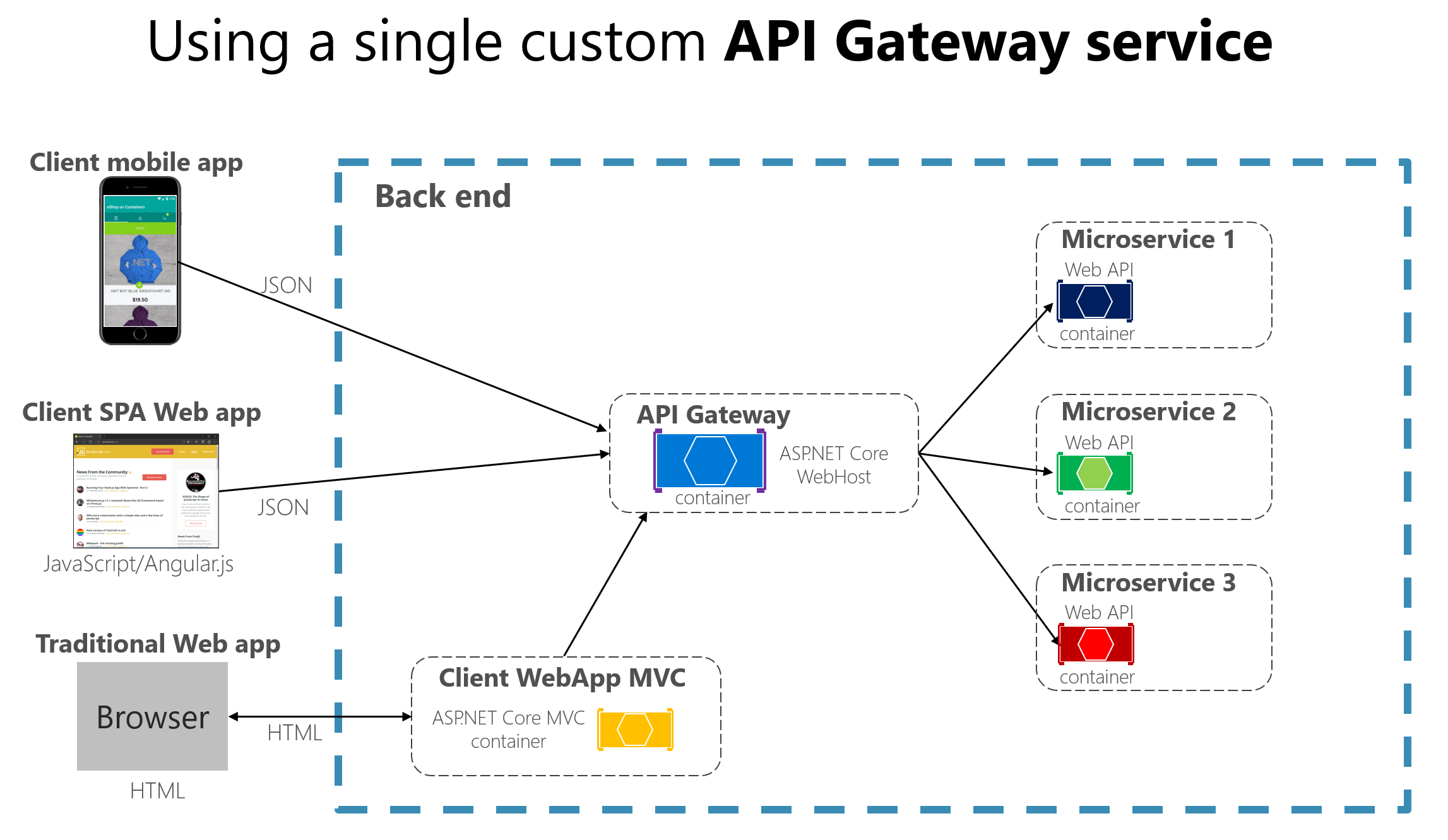
Regularly monitor and assess your API Gateway for vulnerabilities to maintain a high level of security. Implement secure communication protocols to safeguard sensitive data. Consider incorporating defense in depth strategies to add multiple layers of protection.
Ensuring Container Security in Microservices
Another key aspect of container security in microservices is limiting the privileges of your containers. By restricting the permissions granted to each container, you can reduce the impact of a potential breach. It is also important to regularly update and patch your containers to address any known vulnerabilities and keep your system secure.
In addition to these practices, implementing network segmentation can help prevent the spread of a potential breach within your system. By isolating different parts of your network, you can limit the impact of a security incident. Finally, monitoring and logging all container activity is crucial for detecting and responding to any security threats in real-time.
Securing Service-to-Service Communication
By following best practices for microservices security, you can minimize the risk of data breaches and unauthorized access. Ensuring that your services are secure by design and regularly conducting vulnerability assessments can help identify and mitigate potential threats.
Incorporating firewalls and access control mechanisms can add an extra layer of defense, protecting your services from malicious attacks. Regularly monitoring your communication channels and auditing your security measures can help maintain the integrity and reliability of your microservices architecture.
Implementing Shift-Left and DevSecOps Strategies
When implementing **Shift-Left** and **DevSecOps** strategies for **microservices security**, it is essential to prioritize security from the beginning of the development process. By integrating security practices early on, you can identify and address vulnerabilities before they become major risks.
Utilize **continuous integration** and **continuous delivery** pipelines to automate security testing throughout the development lifecycle. This ensures that security measures are consistently applied and any issues are caught early on.
Implement **secure by design** principles to build security directly into your microservices architecture. This includes using encryption, secure communication protocols, and proper access controls to protect sensitive data.
Regularly conduct **vulnerability assessments** and **penetration testing** to identify and remediate any potential weaknesses in your microservices. This proactive approach helps to prevent data breaches and maintain the integrity of your system.
Collaborate closely with **DevOps** teams to align security practices with development processes and promote a **culture of security** across the organization. This partnership is crucial for ensuring that security is a top priority at every stage of the software development lifecycle.
Incorporating Defense-in-Depth Practices
When it comes to securing your microservices architecture, incorporating **Defense-in-Depth Practices** is crucial. This approach involves implementing multiple layers of security measures to protect your system from various threats.
Start by securing your network with firewalls and implementing **Transport Layer Security** to encrypt data in transit. Next, secure your applications by following **Application Security Best Practices** and regularly scanning your code for vulnerabilities.
Additionally, ensure that your interfaces are secure and only accessible to authorized users. By adopting a **Defense-in-Depth Strategy**, you can significantly reduce the risk of a data breach and protect your microservices from potential threats.
Using HTTPS Everywhere for Microservices
When it comes to securing your microservices, **using HTTPS Everywhere** is crucial. By ensuring that all communication between your microservices is encrypted, you can greatly reduce the risk of a data breach. This is especially important in a cloud computing environment where communication protocols are more vulnerable.
Implementing HTTPS Everywhere will not only enhance the reliability and scalability of your microservices, but also improve software quality and overall security. It is considered a best practice in microservices security and can help protect your infrastructure from potential vulnerabilities.
Encrypting and Protecting Secrets
To ensure the security of your microservices, it is crucial to encrypt and protect secrets effectively. Utilize **encryption** techniques to safeguard sensitive information such as API keys, passwords, and tokens. Implement secure storage mechanisms to prevent unauthorized access to these secrets.
Employ **access controls** to restrict who can view or modify sensitive data within your microservices architecture. Utilize tools like HashiCorp Vault or AWS Key Management Service to manage secrets securely. Regularly rotate credentials and keys to minimize the risk of unauthorized access.
Consider integrating **security monitoring** tools into your microservices environment to detect any suspicious activity or potential security breaches. Implement logging and auditing mechanisms to track access to sensitive information. Regularly conduct security audits and vulnerability assessments to identify and address any weaknesses in your system.
By prioritizing the encryption and protection of secrets within your microservices architecture, you can enhance the overall security of your applications and minimize the risk of data breaches.
Understanding Access and Identity Tokens
![]()
Access and identity tokens play a crucial role in securing microservices. These tokens are used to authenticate and authorize users, ensuring that only the right individuals have access to specific resources. By implementing access and identity tokens effectively, you can prevent unauthorized access and data breaches in your microservices architecture. It is important to carefully manage and protect these tokens to maintain the security of your system. Utilizing best practices for access and identity token management, such as regularly rotating tokens and implementing proper encryption, can help enhance the security of your microservices.
Understanding how access and identity tokens work within your microservices ecosystem is essential for maintaining a secure and reliable system.
Prioritizing Container Security
When it comes to **microservices security**, prioritizing **container security** is crucial. Containers are the building blocks of microservices architecture, so ensuring their security is essential for protecting your entire system.
Implementing strict access controls, regular vulnerability scans, and continuous monitoring of containerized applications are key steps in enhancing container security.
Leveraging tools like Docker Security Scanning and Kubernetes Network Policies can help in identifying and mitigating security risks.
Regularly updating containers with security patches, encrypting sensitive data, and segregating containers based on their security levels can further strengthen your container security posture.
By making container security a top priority in your microservices environment, you can significantly reduce the risk of security breaches and protect your system from potential threats.
Centralized Monitoring for Microservices Security
| Centralized Monitoring for Microservices Security | |
|---|---|
| Article Title | Ultimate Guide to Microservices Security Best Practices |
| Centralized Monitoring | Centralized monitoring is essential for ensuring the security of microservices architecture. It allows for real-time monitoring and analysis of all microservices in the system, helping to identify and respond to security threats quickly. |
| Benefits | – Provides visibility into the entire microservices architecture – Helps detect anomalies and security breaches – Enables faster incident response and resolution |
| Tools | – Prometheus – Grafana – ELK Stack (Elasticsearch, Logstash, Kibana) – DataDog |
Incident Response Planning for Microservices
Regular testing and continuous integration can help ensure that any weaknesses are identified and addressed promptly. It is also important to have a plan in place for scaling your security measures as your microservices grow.
Incorporating best practices such as defense in depth and application security can help fortify your microservices against potential threats. Additionally, staying up to date on the latest security trends and technologies can help keep your infrastructure secure in the long run.
By implementing a robust incident response plan for your microservices, you can enhance the reliability and security of your applications, ultimately safeguarding your reputation and ensuring the protection of sensitive information.
Cloud and Cluster Security for Microservices
When it comes to **Cloud** and **Cluster Security** for **Microservices**, there are several best practices to keep in mind. First and foremost, ensure that your microservices are **securely** configured and deployed within your cloud environment. Utilize **firewalls** and other security measures to protect your microservices from unauthorized access and potential **vulnerabilities**.
Implement **secure communication protocols** between your microservices to safeguard the flow of data and information. Regularly conduct **security evaluations** and **vulnerability assessments** to identify and address any potential weaknesses in your microservices architecture.
Additionally, consider implementing **defense in depth** strategies to create multiple layers of security around your microservices.